The New Face of Extortion: How Ransomware Became an Economy
Ransomware has shifted from a technical threat to a business model. It thrives on efficiency, scale, and the fear economy. Organizations must treat extortion events with the same rigor they treat financial audits or legal disputes. And with platforms like AiiR, the power is shifting back to defenders.
Low-code tools are going mainstream
Purus suspendisse a ornare non erat pellentesque arcu mi arcu eget tortor eu praesent curabitur porttitor ultrices sit sit amet purus urna enim eget. Habitant massa lectus tristique dictum lacus in bibendum. Velit ut viverra feugiat dui eu nisl sit massa viverra sed vitae nec sed. Nunc ornare consequat massa sagittis pellentesque tincidunt vel lacus integer risu.
- Vitae et erat tincidunt sed orci eget egestas facilisis amet ornare
- Sollicitudin integer velit aliquet viverra urna orci semper velit dolor sit amet
- Vitae quis ut luctus lobortis urna adipiscing bibendum
- Vitae quis ut luctus lobortis urna adipiscing bibendum
Multilingual NLP will grow
Mauris posuere arcu lectus congue. Sed eget semper mollis felis ante. Congue risus vulputate nunc porttitor dignissim cursus viverra quis. Condimentum nisl ut sed diam lacus sed. Cursus hac massa amet cursus diam. Consequat sodales non nulla ac id bibendum eu justo condimentum. Arcu elementum non suscipit amet vitae. Consectetur penatibus diam enim eget arcu et ut a congue arcu.

Combining supervised and unsupervised machine learning methods
Vitae vitae sollicitudin diam sed. Aliquam tellus libero a velit quam ut suscipit. Vitae adipiscing amet faucibus nec in ut. Tortor nulla aliquam commodo sit ultricies a nunc ultrices consectetur. Nibh magna arcu blandit quisque. In lorem sit turpis interdum facilisi.
- Dolor duis lorem enim eu turpis potenti nulla laoreet volutpat semper sed.
- Lorem a eget blandit ac neque amet amet non dapibus pulvinar.
- Pellentesque non integer ac id imperdiet blandit sit bibendum.
- Sit leo lorem elementum vitae faucibus quam feugiat hendrerit lectus.
Automating customer service: Tagging tickets and new era of chatbots
Vitae vitae sollicitudin diam sed. Aliquam tellus libero a velit quam ut suscipit. Vitae adipiscing amet faucibus nec in ut. Tortor nulla aliquam commodo sit ultricies a nunc ultrices consectetur. Nibh magna arcu blandit quisque. In lorem sit turpis interdum facilisi.
“Nisi consectetur velit bibendum a convallis arcu morbi lectus aecenas ultrices massa vel ut ultricies lectus elit arcu non id mattis libero amet mattis congue ipsum nibh odio in lacinia non”
Detecting fake news and cyber-bullying
Nunc ut facilisi volutpat neque est diam id sem erat aliquam elementum dolor tortor commodo et massa dictumst egestas tempor duis eget odio eu egestas nec amet suscipit posuere fames ded tortor ac ut fermentum odio ut amet urna posuere ligula volutpat cursus enim libero libero pretium faucibus nunc arcu mauris sed scelerisque cursus felis arcu sed aenean pharetra vitae suspendisse ac.
The New Face of Extortion: How Ransomware Became an Economy
The rise of digital extortion is no longer just a technical problem. It’s an economic machine. Welcome to the new ransomware economy.
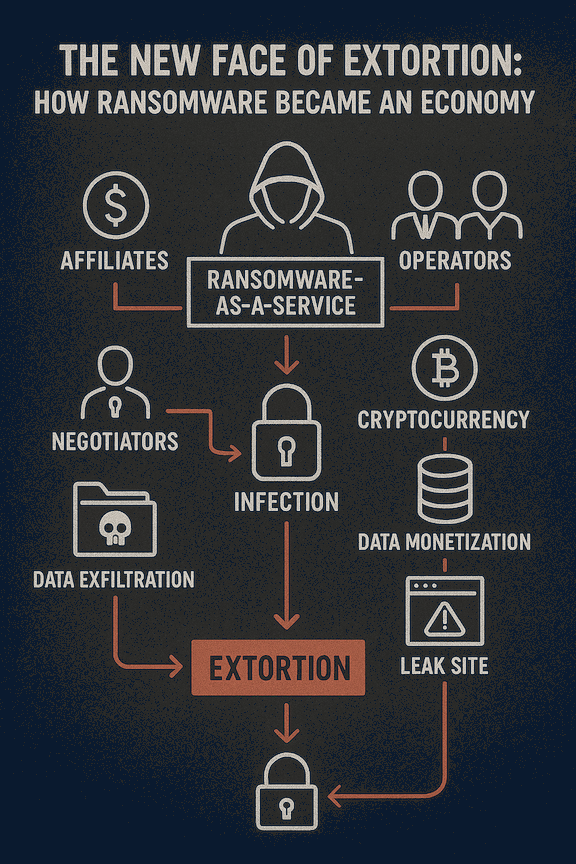
The Industrialization of Ransomware
Over the past five years, ransomware has evolved from a lone wolf hacker scheme into a full-blown industrialized operation. Today, it mirrors the structure of a legitimate business: affiliates, support desks, pricing calculators, marketing teams (on the dark web), and even customer service. This is the world of Ransomware-as-a-Service (RaaS).
These operations allow even low-skilled threat actors to launch sophisticated attacks by subscribing to RaaS platforms. The result? A boom in ransomware incidents, driving billions in illicit revenue annually.
What Drives the Ransomware Economy?
Several key forces are propelling the growth of the extortion market:
- Cryptocurrency: Pseudonymous payments make it easy to transfer funds across borders without detection.
- Data Monetization: Stolen data has multiple value layers—extortion, resale, identity theft.
- Leak Sites: Public shame is now a weapon. Victims face pressure not just from encryption, but from exposure.
- Insurance: Some cyber insurance policies historically covered ransom payments, making it a viable path for fast resolution.
Meet the New Threat Actor
Modern ransomware actors aren't lone hackers. They are:
- Affiliates: Contractors using ransomware kits to launch attacks and share profits.
- Operators: Core groups managing infrastructure, payloads, and negotiations.
- Negotiators: Specialized team members who handle victim communication.
- AI Augmentation: Some threat groups are now using language models to draft negotiation messages, conduct sentiment analysis, and stage psychological pressure tactics.
Extortion, Not Just Encryption
Today's attacks rarely rely on just locking files. Double and triple extortion models have become standard:
- Encrypt data
- Exfiltrate sensitive files
- Threaten public leaks or contact your customers/regulators
The goal is not disruption. It's leverage.
How AiiR Fits In
The AiiR platform was purpose-built for this new reality. With CEIRA—the Counter Extortion Incident Response AI—it helps breach coaches and security teams respond with speed, intelligence, and control.
- Profile threat actors and identify RaaS tools
- Automate early negotiation responses
- Coordinate secure crypto payments
- Integrate with blockchain forensic tools
Ransomware isn’t going away. But how we respond can evolve.
