Intelligence EnRiched
Correlated & Enriched Case Intelligence
Correlates global threat feeds, internal logs, and forensic tools into one AI-automated analysis engine—with visualized MITRE mapping and predictive attacker insights.
Live Threat Intelligence Aggregation
Integrates OSINT, dark web crawlers, EDR, and forensic tools (e.g., Autopsy, Wireshark) into a single intelligence layer. Enrichment pipelines flag TTPs and IOC correlations.
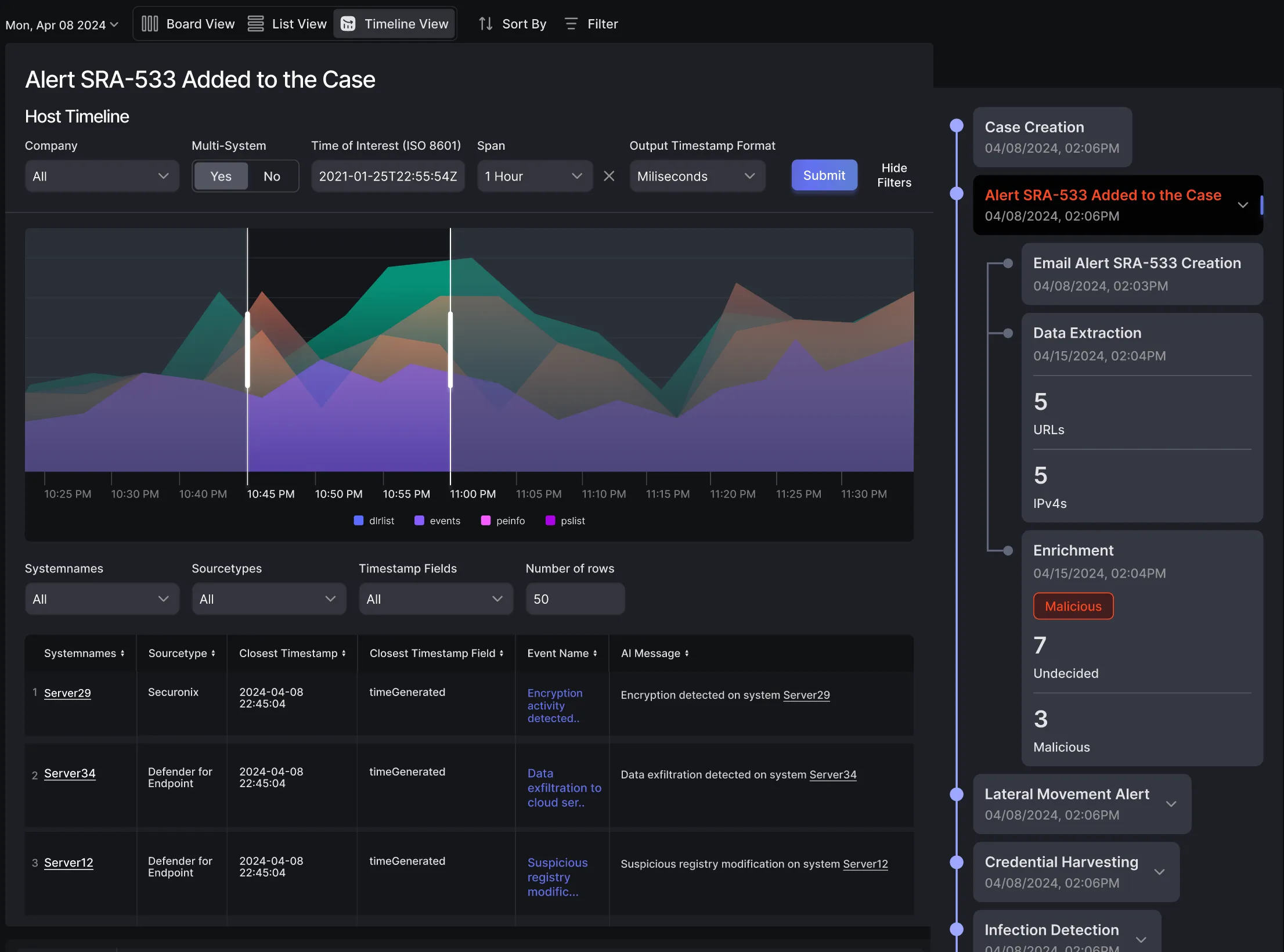
Root Cause & MITRE ATT&CK Correlation
AI-assisted root cause analysis maps incidents to MITRE framework and generates an attack chain visual timeline for each case, enhancing both forensic clarity and legal defensibility.
Behavioral Threat Modeling & Actor Profiling
Detect adversary patterns using ML-driven behavior analysis. CEIRA predicts next steps based on evolving attacker intent and campaign signals.
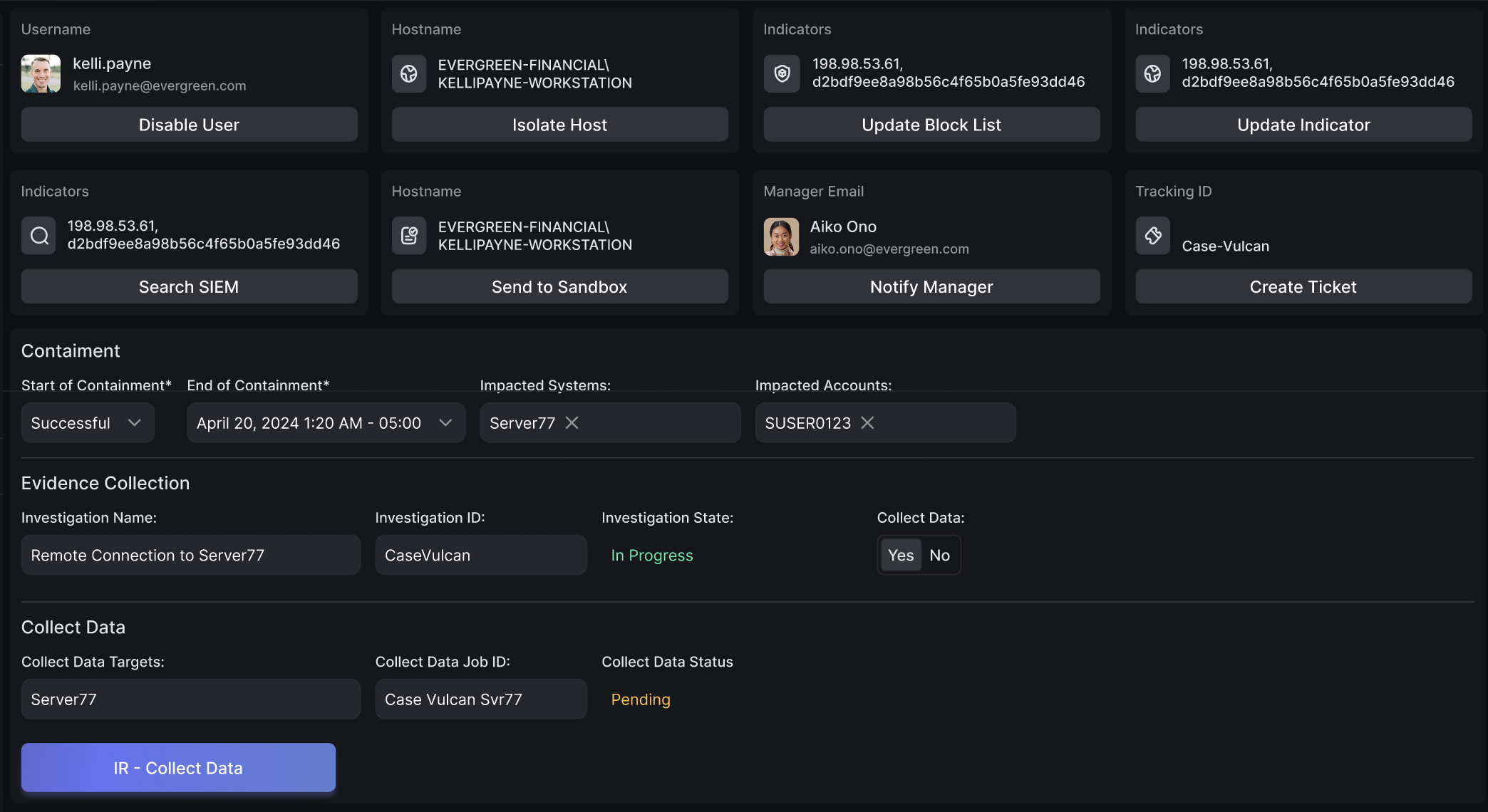
Threat Containment & Automated Remediation
Trigger EDR and containment integrations (CrowdStrike, SentinelOne, Defender) from AiiR's interface to isolate users, systems, or assets. Recovery playbooks support both automated and human-in-the-loop actions.
Intelligence EnRiched
Investigation Analysis & Threat Intelligence
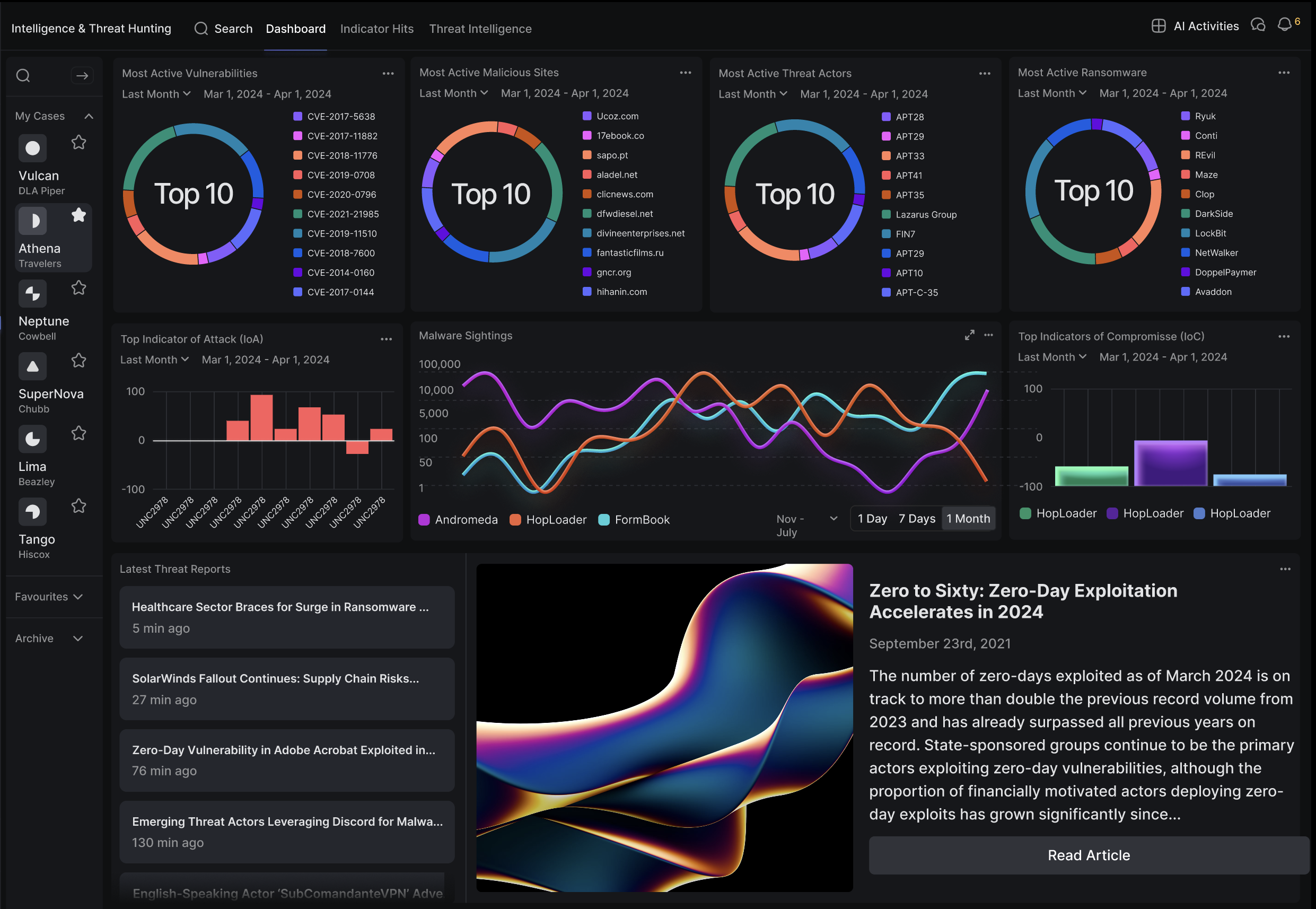
Live Threat Intelligence Aggregation
Integrates OSINT, dark web crawlers, EDR, and forensic tools (e.g., Autopsy, Wireshark) into a single intelligence layer. Enrichment pipelines flag TTPs and IOC correlations.
Root Cause & MITRE ATT&CK Correlation
AI-assisted root cause analysis maps incidents to MITRE framework and generates an attack chain visual timeline for each case, enhancing both forensic clarity and legal defensibility.
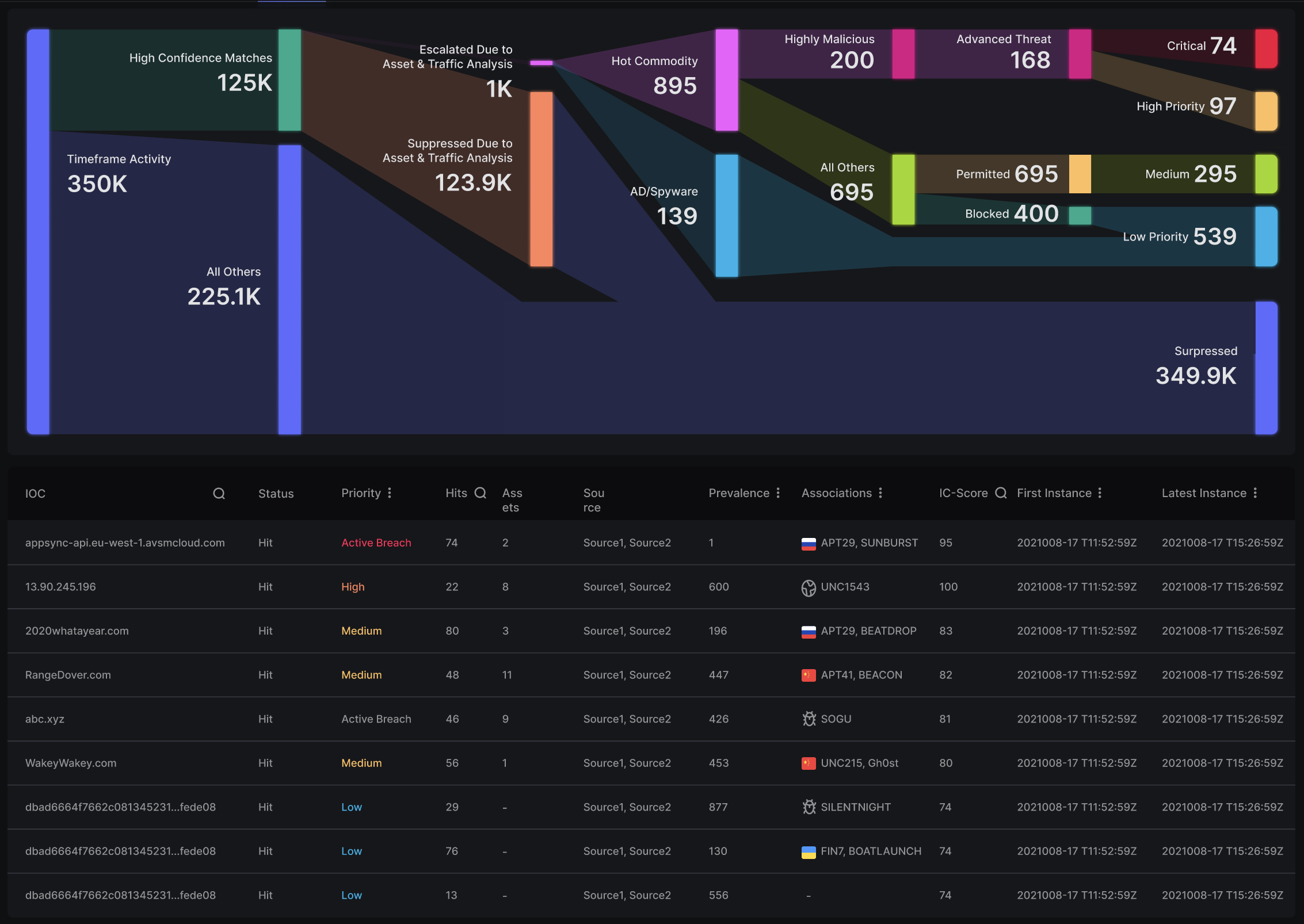
Behavioral Threat Modeling & Actor Profiling
Detect adversary patterns using ML-driven behavior analysis. CEIRA predicts next steps based on evolving attacker intent and campaign signals.
Threat Containment & Automated Remediation
Trigger EDR and containment integrations from AiiR’s interface to isolate users, systems, or assets. Recovery playbooks support both automated and human-in-the-loop actions.